ONSITE • REMOTE • CLOUD
What Is L3?
We help you to resolve your most advanced tool alerts, using all our DFIR / TH expertise to investigate then when your SOC or internal team is not capable
L3 (Level 3 Expert Escalations) is a specialized cybersecurity service designed to handle the most complex and unresolved security incidents escalated by an organization's SOC. Our expert team of Threat Hunters (TH), Digital Forensics & Incident Response (DFIR) specialists, and Cyber Threat Intelligence (CTI) analysts conduct deep investigations, validate threats, and provide actionable recommendations to mitigate security risks effectively.
Why Should You Use L3?
Traditional SOC teams often face challenges when dealing with sophisticated threats that require advanced analysis beyond Level 1 and Level 2 capabilities. L3 Expert Escalations ensure:
- Advanced Investigation & Analysis – Leveraging deep expertise to analyze unresolved security alerts.
- Reduction of False Positives – Distinguishing between false alarms and real threats with precision.
- Accelerated Response – Enabling faster and more accurate decision-making to mitigate potential security breaches.
- Access to Elite Expertise – Engaging a team of highly specialized analysts with experience in real-world cyber threats.
- Comprehensive Reporting & Recommendations – Delivering detailed findings, conclusions, and strategic recommendations to enhance security posture.
Methodology
Our L3 Expert Escalation process follows a structured approach to ensure accuracy and efficiency in incident handling:
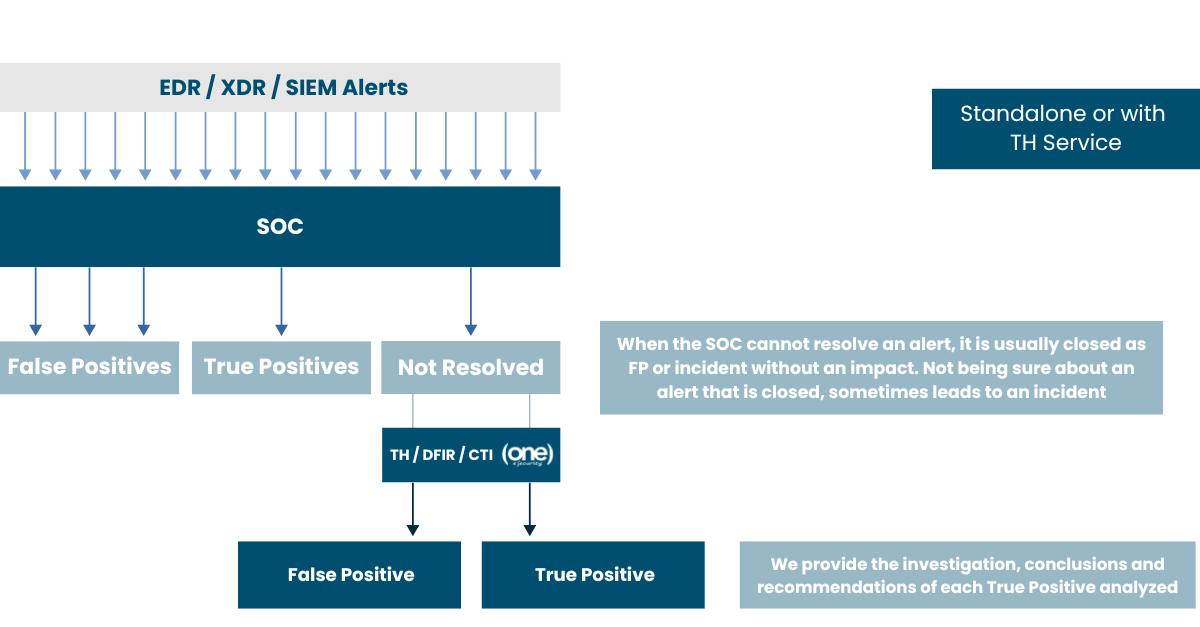
Alert Generation & Initial Analysis
- Security alerts are triggered by various detection technologies such as EDR, XDR, SIEM, and other security platforms.
- The SOC team performs an initial triage to classify alerts as false positives, true positives, or not resolved.
Escalation to One eSecurity
- Not resolved alerts are escalated to One eSecurity’s expert team for in-depth investigation.
- Our Threat Hunting (TH), Digital Forensics & Incident Response (DFIR), and Cyber Threat Intelligence (CTI) specialists conduct a comprehensive analysis.
Advanced Investigation
Our experts determine whether the escalated case is a false positive or a true positive by utilizing:
- Behavioral and forensic analysis.
- Correlation with threat intelligence sources.
- Advanced anomaly detection techniques.
Findings & Validation
- If the alert is confirmed as a true positive, our team provides a full investigation report, including:
Root cause analysis.
- Attack chain reconstruction.
- Attribution insights based on threat intelligence.
- Recommended mitigation and containment strategies.
If the alert is identified as a false positive, we document the findings and provide recommendations to improve detection rules and reduce false alarms.
Strategic Recommendations & Reporting
Detailed reports are provided to the SOC team, including:
- Investigation summary.
- Conclusions and impact assessment.
- Actionable recommendations for remediation and future prevention.
The SOC can integrate these findings to refine detection capabilities and enhance their overall security framework.
Contact Us
Ensure your organization has access to top-tier cybersecurity expertise with our L3 Expert Escalation service. Contact One eSecurity today to learn how we can enhance your incident response capabilities and protect your business from advanced cyber threats.
📩 Request more information at sales@one-esecurity.com
⚠️ Experiencing a cyberattack? REPORT AN INCIDENT
Related To Our Services
| Digital Forensics and IR | Emergency Incident Response | Cyber Threat Intelligence |
|---|---|---|
| One eSecurity Digital Forensics service is focused on system in-depth analysis, aiming at obtaining a traceable record of previous activity in order to answer any investigative questions. | One eSecurity Emergency Incident Response is aimed at clients who need agile response and support when a security incident happens. | The Cyber Threat Intelligence service by One eSecurity provides (both internally and for clients) knowledge and information on key threats for decision-making and forecasts of risk situations on IT systems and networks. |
| Learn more | Learn more | Learn more |
