ONSITE • REMOTE • ONLINE • CLOUD
What Is SKaaS?
SKaaS (SKY as a Service) is a first next-generation service, completely focused on providing advanced digital investigation & forensic capabilities to Computer Incident Response Teams (CERTs).
In particular, the SKaaS model serves as the first phase in any incident handling situation, enabling forensic analysts and investigators to perform their tasks without the overhead cost of deploying and maintaining their own forensics work environments.
SKaaS addresses the following main issues:
Investment, Maintenance, and Procurement of Specialized Resources
- Companies require specialized investigative resources (forensic analysts) that have the capability to analyze and respond after a security incident. These resources must be experts in the forensic field, turning them into highly valued and sought after profiles, difficult to find in the market. Providing these analysts with the necessary material (laboratory, forensic hardware and software), and maintaining it over time, implies a continuous outlay and an initial investment that is difficult to justify, especially when the number of cases to be analyzed is small, the investment to be amortized is large and the return on investment is unclear.
Incident Response and Forensic Team Availability
- The sizing of incident response teams is not always adequate to the needs of the cybersecurity department. In many cases, potential security failures and violations are overlooked due to other more critical incidents simply because the number of resources is insufficient.
Maturity Level
- The maturity level of IR Plans and procedures is not always optimal for responding to security incidents. SKaaS provides a methodological approach based on standards and methods that can help you with your cybersecurity incidents.
Why Should You Use SKaaS?
SKaaS provides the solution to many of the challenges that clients currently face, whether it is responding to incidents or conducting forensic investigations locally and in remote locations. Some of those challenges are:
- Increasing number of cases per day, across many different countries and time zones.
- Many different types of cases with increasing complexity.
- Multiple and simultaneous cases with different degrees of sensitivity.
- Higher device diversity and increasingly number of devices.
- Devices with larger capacity and storage therefore larger volumes of evidence.
- More complexity in apps as well as encryption frequently found.
- A shorter response time is required at the same time as limited number of human resources in Incident Response and Forensic teams.
- Time and resources assigned to deploy and maintain complex forensic laboratories mean little time is available for investigation tasks.
- Investigators often work simultaneously on many different cases, where collaboration among different investigators is also critical.
- Multiple tools and approaches to conduct investigations of the same evidence.
- Complex environments prone to case and evidence contamination.
Our Service
SkaaS is a Digital Forensic and Incident Response (DFIR) service remotely managed and operated by the One eSecurity team. This service combines traditional forensics processes and best practices, the SKY investigative framework and a dashboard to interact with analysts in charge of cases.
Every time the client opens a case, a Principal Analyst (named proctor) contacts the client to find out the details of the incident and advise the client on how to proceed and what evidence must be acquired.
SKaaS Dashboard
Once registered in the service, the client receives the credentials to access the dashboard, which allows the client company to perform the following tasks:
- Request the opening of cases and provide the details of the investigation.
- Check the status of its cases.
- Interact with One eSecurity analysts carrying out investigative work on the case.
- Follow up the research lines carried out.
- Access its reports, outputs, and findings.
- Download the outputs.
- Administrative management: access control, registration, and cancellation of the registered users defined by the client company.
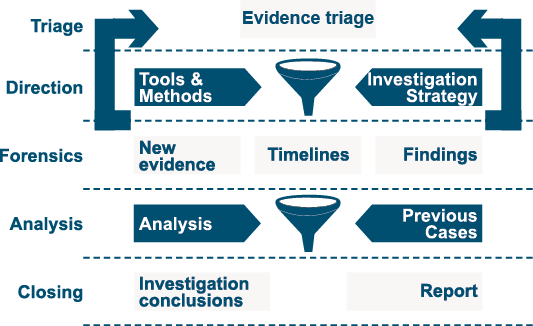
Forensic Process and Methodology
The following picture illustrates the forensic and investigation process carried out by our team:
SKY Technology
SKY is a state-of-the-art advanced digital platform that gives support to investigation and response teams for digital forensic investigation and analysis processes. SKY consists of a platform based on a virtualization infrastructure for the acquisition and processing of digital evidence, the deployment of specialized tools in the digital forensic field and high capacity storage.
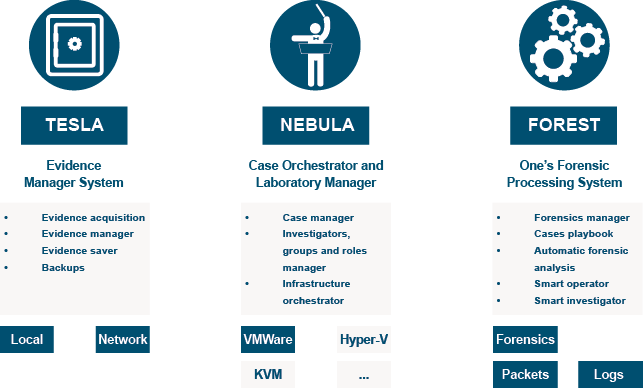
SKY orchestrates the different components and offers advanced capabilities for both electronic evidence management (TESLA) and forensic laboratory management and operations (NEBULA). This combination allows the complete management of a case lifecycle: creation, evidence loading, processing, result generation, and forensic reports. SKY is a multi-tenant solution that keeps each client company, with its cases and evidence, completely isolated from the rest.
Evidence management
- Encrypted upload of evidence to our secure storage system.
- Storage and categorization of evidence. Chain of custody secured.
- Hash calculations, metadata generation, and chain of custody.
- Prioritization of transfers to the backend.
- Global repository of unchanging evidence.
- Copies of the master evidence for the analysts to work on.
- Support for evidence stored in encrypted containers (Bitlocker, Truecrypt, and LUKS).
Forensic lab management
- Global case management.
- Deployment of forensic analysis machines, malware analysis machines, network traffic machines, case-specific wikis.
- Creation of a database with all the information of every case, as well as the associated data: evidence records, chain of custody records, hashes, analysis results, reports, etc.
- Isolated environment per case. There is no visibility of the rest of the cases or the rest of the forensic labs.
- There are no possible ways to contaminate environments, which means that other components cannot be infected.
- Own networking and VLAN assignment. Assignment of IP range to each of the machines in the case creation of its entry in the DNS.
- Creation and maintenance of an internal DNS and separate networks of the laboratory. Multilayer approach.
- Forensic templates with more than a hundred forensic tools already installed, deployed in an automated way.
- All virtual machines in the same case have visibility of the same evidence.
- Creation of access rules in the firewalls for each of the machines that are deployed.
- NFS configuration for evidence mapping and sharing. Continuous process for each of the machines as well as for each of the cases.
- Dynamic environment: if the case grows, there is an assignment of new evidence, and the growth of volumes of evidence analysis is automatically done.
- Cloning of computers, hostname changes, and customization of items that could conflict on the same network.
- Shared assignment of forensic tools licenses.
- Backup execution and restoration.
- Case pause, case closure. Restoration of closed to open cases.
Investigators management
- Volumes of evidence in RO or RW analysis, specific to the case, and without visibility of the rest.
- Access control.
- Deployment of a two-factor authorization (2FA) mechanism to access the research platform.
- Access to cases is done through a broker in which the accesses are registered, and a log is kept.
- Assignment of sessions for each of the users.
- Creation of a custom Virtual Desktop Interface (VDI) for each user.
- Assignment of new created users to existing cases.
- Creation of public keys for each computer to be able to operate Single Sign-On (SSO) functions.
- Creation and maintenance of an LDAP.
Related To Our Services
| Emergency Incident Response | Cyber Threat Intelligence | Cyber Consulting |
|---|---|---|
| One eSecurity Emergency Incident Response is aimed at clients who need agile response and support when a security incident happens. | The Cyber Threat Intelligence service by One eSecurity provides (both internally and for clients) knowledge and information on key threats for decision-making and forecasts of risk situations on IT systems and networks. | One eSecurity CYCON service can give you honest answers to the most complex questions and acting as a guide throughout decision-making processes. |
| Learn more | Learn more | Learn more |
