ONSITE • REMOTE • CLOUD
What Is CTI?
One eSecurity’s Cyber Threat Intelligence Service offers our clients intelligence management and processing on three levels: strategic, operational, and tactical. We provide intelligence planning, collection, processing, exploitation, analysis, and production, as well as the dissemination and feedback of relevant intelligence.
Why Should You Use CTI?
The number of threats and their typology have expanded, and the actors are more numerous and increasingly professional. Nowadays, any organization is vulnerable, be it through social engineering techniques, such as phishing email campaigns, or through more sophisticated means, such as zero-day vulnerability exploits. As a result, it is paramount to focus efforts on the organization’s hotspots and vulnerabilities in order to be one step ahead.
One eSecurity’s CTI service responds to these needs by providing organizations with the necessary knowledge about threats, actors, tactics, techniques, and vulnerabilities in the environment, and providing our clients with customized and tailored intelligence products. One eSecurity’s approach to the intelligence cycle is supported by adapting processes, products, and flows that achieve the most appropriate use of intelligence for each scenario and client.
The service comprises the following phases:
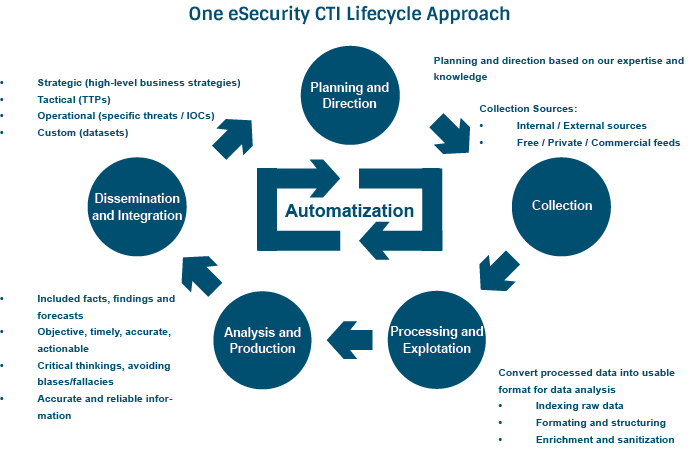
| Phases | Description |
| Planning and Direction | We collaborate and provide advice on the Cyber Threat Intelligence Plan that the organization needs to adopt, by developing the capacities that may be needed and managing them from a service perspective or along with the client in the performance and development of these capacities. |
| Collection | At One eSecurity, we are a source of information, in conjunction with the identification and assessment of sources of information both in the public and private realms. We carry out research processes to identify the necessary sources that respond to the highlighted needs and requirements. |
| Processing and Exploitation | We design, model, assess, collaborate, and implement tools aimed at managing intelligence information, from OSINT environment to the development of a Threat Intelligence Platform (TIP). We adapt and customize the design to the organization at all levels of architecture, drawing on automation as a reference of evolution in intelligence systems. |
| Analysis and Production | The One eSecurity team analyzes the information available and identifies new threats, compromise indicators, actors, and campaigns that can affect the organization, generating customized reports, lists of indicators and detection rules, graphical models, and even new threat alerts. |
| Dissemination | We work together with different organizations that show interest in sharing and creating a community to prevent cybersecurity incidents. We support and advice clients as to how and what should be shared and disseminated, according to the policies and context of each organization. |
What Advantages Do We Offer Compared To Our Competitors?
Experience
We have experience of developing our Cyber Threat Intelligence capacities after countless incidents. During an investigation, we issue valuable information and indicators that can be used to estimate the reach, as well as the investigation threads to follow. We also have a team of certified professionals who work continuously to collect and analyze information.
Effectiveness
Effectiveness at work lies within our DNA, maximizing the effort we put into optimized solutions, being guided by intelligence, applicability, and the use of valuable information.
Flexibility
We adapt all our organizational experience, making models and customizing solutions, and avoiding black box solutions. The CTI processes and technologies are integrated into the organization establishing common flows both with internal departments or teams, as well as with third parties.
Trust
We establish trust relationships with our clients, giving the best we have and the most appropriate solutions to present and future problems. We provide advice in close proximity, using our knowledge and managing the threat together.
Related To Our Services
| Threat Hunting | Emergency Incident Response | Cyber Consulting |
|---|---|---|
| Our Threat Hunting service combines the analytic capacity of our most experienced experts with the power and automation of our Hunting Framework, offering a continuous and proactive threat search process in both networks and systems. | One eSecurity Emergency Incident Response is aimed at clients who need agile response and support when a security incident happens. | One eSecurity CYCON service can give you honest answers to the most complex questions and acting as a guide throughout decision-making processes. |
| Learn more | Learn more | Learn more |
